Here’s how to create a site-to-site VPN between StrongSwan and SonicWall. This has been tested with Ubuntu 14.04 and StrongSwan 5.1.2, and SonicWall with SonicOS 5.9 at the other end.
Table of Contents
Network Topology
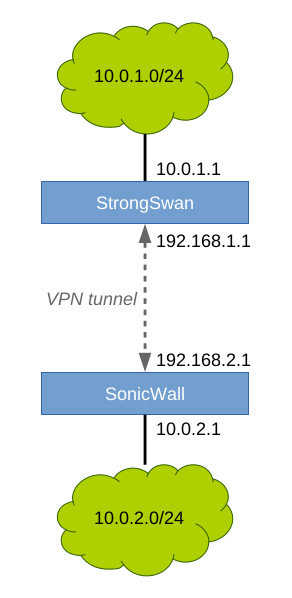
In this example, we will route traffic between two networks that are located at different sites. Our example network topology looks like this:
The VPN tunnel will encrypt all traffic between the endpoints. The green networks will be routed to each other through the encrypted tunnel.
StrongSwan
Install
|
1 |
sudo apt-get install strongswan |
Configure
Two files need editing: /etc/ipsec.conf and /etc/ipsec.secrets. The first one is the configuration file, and the second one contains the pre-shared key the endpoints will use to authenticate each other.
/etc/ipsec.conf:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
conn sonicwall # This server left=192.168.1.1 leftid=192.168.1.1 # The network behind this server leftsourceip=10.0.1.1 leftsubnet=10.0.1.0/24 # The remote SonicWall right=192.168.2.1 rightid=192.168.2.1 # The network behind remote SonicWall rightsubnet=10.0.2.0/24 # Connection parameters keyexchange=ikev2 authby=psk ike=aes256-sha1-modp2048 esp=aes256-sha1-modp2048 auto=start |
We use IKEv2 for key exchange, with AES-256 for encryption and SHA-1 for hashing. A 2048-bit key means Diffie-Hellman group 14. Authentication is done using a pre-shared key. The connection will be started automatically at start.
/etc/ipsec.secrets:
|
1 |
192.168.1.1 192.168.2.1 : PSK "XXXSECRETXXX" |
There should be one line per connection in that file. The format, when using pre-shared keys, is this:
|
1 |
local_ip remote_ip : PSK "your password" |
Please set your password to a random string.
Start IPsec Service
To start the service:
|
1 |
sudo service ipsec start |
To make it start at boot:
|
1 |
sudo update-rc.d ipsec defaults |
To see the status, run:
|
1 |
sudo ipsec statusall |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
Status of IKE charon daemon (strongSwan 5.1.2, Linux 3.13.0-48-generic, x86_64): uptime: 92 seconds, since Apr 04 14:45:29 2015 malloc: sbrk 2433024, mmap 0, used 351664, free 2081360 worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 2 loaded plugins: charon test-vectors aes rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pkcs1 pkcs7 pkcs8 pkcs12 pem openssl xcbc cmac hmac ctr ccm gcm attr kernel-netlink resolve socket-default stroke updown eap-identity addrblock Listening IP addresses: 192.168.1.1 10.0.1.1 Connections: sonicwall: 192.168.1.1...192.168.2.1 IKEv2 sonicwall: local: [192.168.1.1] uses pre-shared key authentication sonicwall: remote: [192.168.2.1] uses pre-shared key authentication sonicwall: child: 10.0.1.0/24 === 10.0.2.0/24 TUNNEL |
However, you need to configure the other endpoint first before you will see an active connection and a security association.
SonicWall
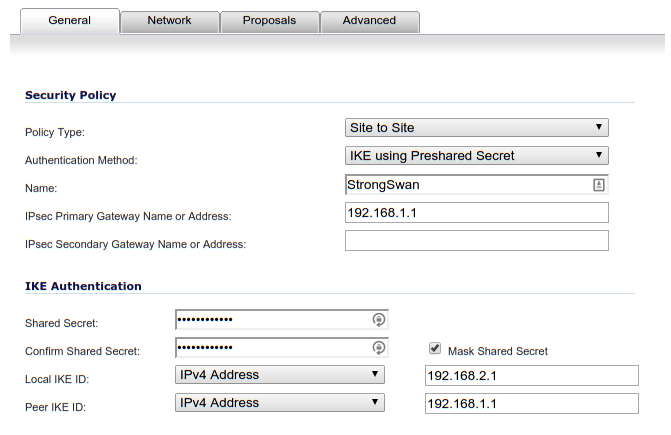
Go to VPN > Settings. Add a new VPN connection.
VPN Connection > General
The “Shared Secret” field should contain the same random string you put into the /etc/ipsec.secrets file.
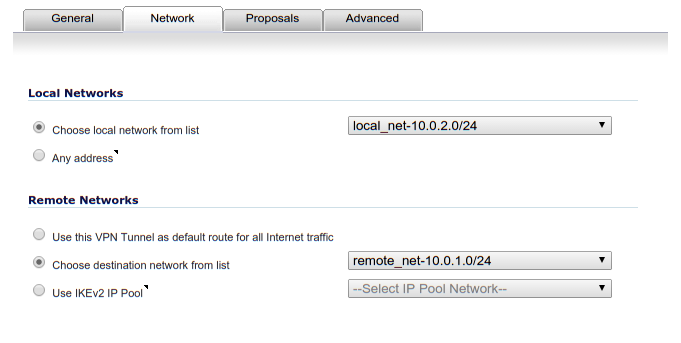
VPN Connection > Network
The remote network zone should be a “VPN” zone.
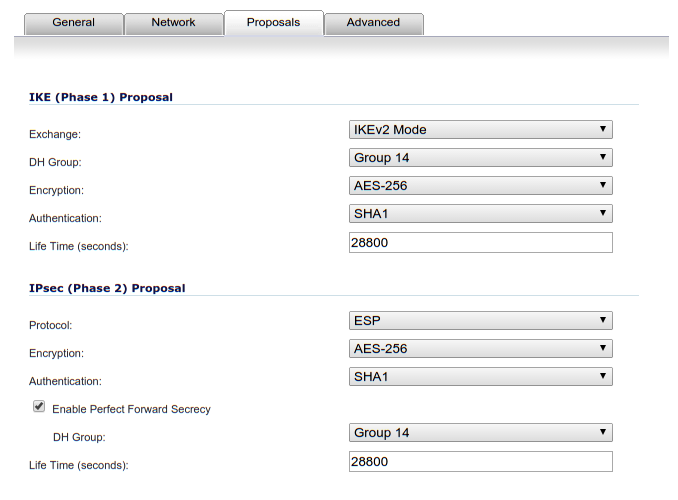
VPN Connection > Proposals
For the proposal we must match the parameters in /etc/ipsec.conf.
VPN Connection > Advanced
In the advanced tab I enabled keep-alive.
Firewall Rules
Also, remember to add firewall rules to allow traffic to flow between networks in SonicWall. Also do the same if you have Iptables in use on the StrongSwan server.
Check Status
At this point, the SonicWall should show a green dot on the VPN policy line you created. If not, check the SonicWall log for error messages.
You should also be able to see an active security association on the StrongSwan host with:
|
1 |
sudo ipsec statusall |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
Status of IKE charon daemon (strongSwan 5.1.2, Linux 3.13.0-48-generic, x86_64): uptime: 92 seconds, since Apr 04 14:45:29 2015 malloc: sbrk 2433024, mmap 0, used 351664, free 2081360 worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 2 loaded plugins: charon test-vectors aes rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pkcs1 pkcs7 pkcs8 pkcs12 pem openssl xcbc cmac hmac ctr ccm gcm attr kernel-netlink resolve socket-default stroke updown eap-identity addrblock Listening IP addresses: 192.168.1.1 10.0.1.1 Connections: sonicwall: 192.168.1.1...192.168.2.1 IKEv2 sonicwall: local: [192.168.1.1] uses pre-shared key authentication sonicwall: remote: [192.168.2.1] uses pre-shared key authentication sonicwall: child: 10.0.1.0/24 === 10.0.2.0/24 TUNNEL Security Associations (1 up, 0 connecting): sonicwall[2]: ESTABLISHED 86 seconds ago, 192.168.1.1[192.168.1.1]...192.168.2.1[192.168.2.1] sonicwall[2]: IKEv2 SPIs: XXX XXX*, pre-shared key reauthentication in 2 hours sonicwall[2]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048 sonicwall{2}: INSTALLED, TUNNEL, ESP SPIs: XXX XXX sonicwall{2}: AES_CBC_256/HMAC_SHA1_96, 7224 bytes_i (86 pkts, 1s ago), 7224 bytes_o (86 pkts, 1s ago), rekeying in 44 minutes sonicwall{2}: 10.0.1.0/24 === 10.0.2.0/24 |
You can control your tunnel(s) with these commands:
|
1 2 |
sudo ipsec down sonicwall sudo ipsec up sonicwall |
See log files /var/log/auth.log and /var/log/syslog for log messages.
Hello,
Is this a host to host vpn or site to site? Because from my server which contains strongswan now. I can ping to the other subnet as well. But I am not able to do it from some other device.
Hello!
I think I’m doing something wrong, did all of this but still not working.
I have an EC2 instance on AWS with Strongswan and I need connect to a Sonicwall of the client, I make all without sucess, folow the configuration
config setup
strictcrlpolicy=no
uniqueids = yes
charondebug=”all”
conn truckpad-vpn
# This server
left=10.31.20.xxx
leftid=34.208.127.xxx
# The network behind this server
leftsourceip=10.31.20.xxx
leftsubnet=10.31.20.0/32
leftfirewall=yes
# The remote SonicWall
right=179.191.85.xxx
rightid=192.168.2.xxx
# The network behind remote SonicWall
rightsubnet=192.168.3.128/32
# Connection parameters
keyexchange=ikev1
authby=psk
ike=aes256-sha1-modp1024!
esp=aes256-sha1-modp1024!
auto=start